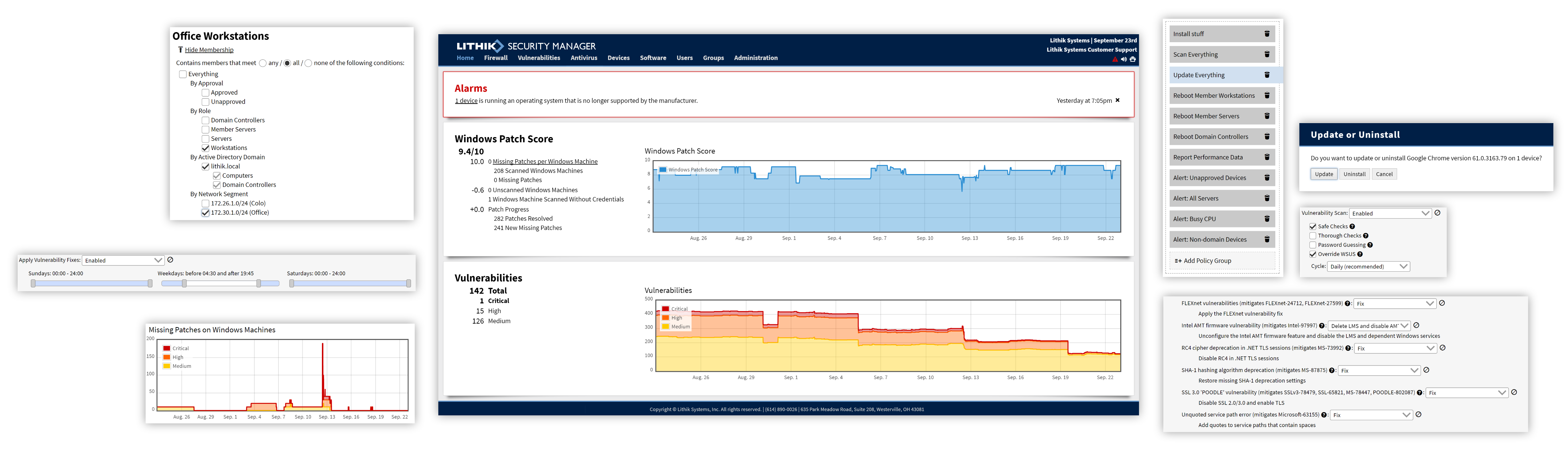
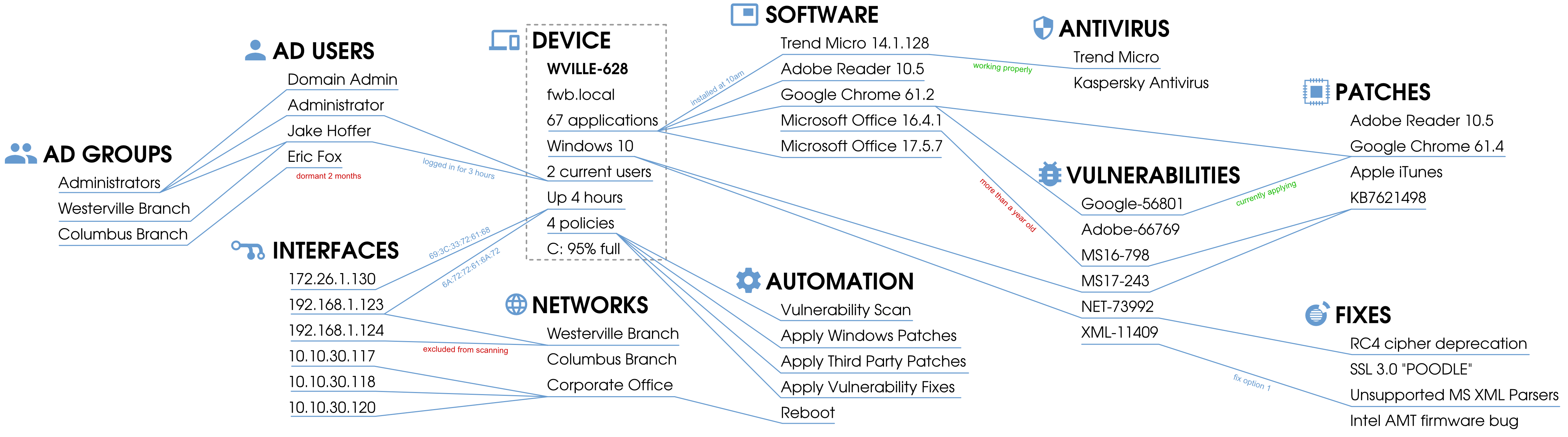
Don't just protect vulnerabilities from attack; remove them entirely. Automatically applying patches and fixing insecure configurations drastically reduces the number of ways a hacker even has a chance to get in.
Lithik Security Manager: The Ultimate Security Management Tool