The Lithik Security Manager can automatically apply every patch as soon as it is available.
In 18 years of operation, we've never had a customer experience a reportable breach.
More than 80% of US companies have been breached in the last 12 months.
SET UP A DEMO
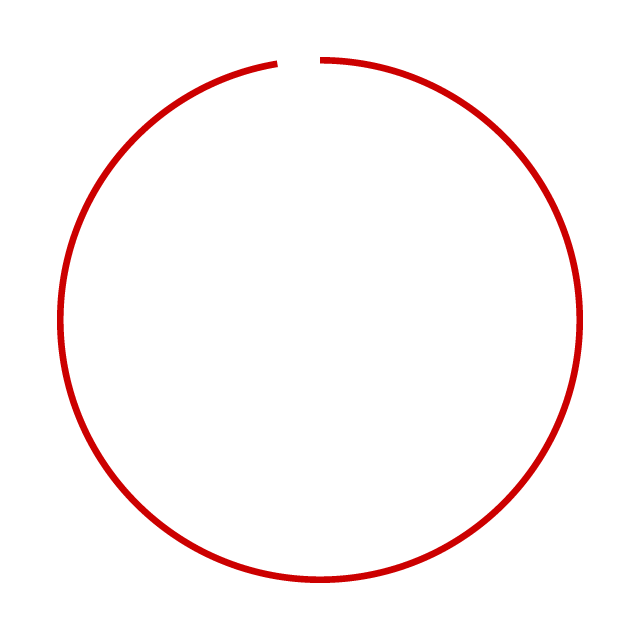
97% of companies are highly vulnerable from missing patches.
How can you be sure you are in the 3%?
Patching is not sexy. Nobody goes into IT to apply patches all day.However, the truth is that out-of-date patches are the number one reason your network is vulnerable.
The Lithik Security Manager eliminates your patchable vulnerabilities.
SET UP A DEMO
Your blueprint for automated security
Competing products offer tools that help you get your regular workload done in slightly less time. The Lithik Security Manager does the work for you. You set the policies deciding which machines should be scanned, which updates to apply, and timing for action.
For a typical, medium-sized network, Lithik can help you get these set up over the course of a 15-30 minute phone call. Next, the Lithik Security Manager will automatically handle your scanning and updating, including new devices and software installations.
For a typical, medium-sized network, Lithik can help you get these set up over the course of a 15-30 minute phone call. Next, the Lithik Security Manager will automatically handle your scanning and updating, including new devices and software installations.
1
Schedule a 30-minute call with Lithik
Schedule a 30-minute call with Lithik
2
Choose your policies
Choose your policies
3
Focus on other priorities
Focus on other priorities
SET UP A DEMO
Your customers' trust is your most valuable asset.
Just take it from some of ours:
My IT staff used to stay until midnight on Patch Tuesdays to get everything applied; now with the Lithik Security Manager they don't work late that day anymore. I would have to hire additional IT staff to cover all the things the Lithik Security Manager does.
Chad Hoffman, President and CEO
Richwood Bank
Chad Hoffman, President and CEO
Richwood Bank
I trust the Lithik Security Manager to keep my environment patched and up to date. The ability to reliably patch third party software has eluded us for a long time due to budgetary and time constraints; the Lithik Security Manager has cured that problem.
Greg Lawless, IT Manager
Over 400 workstations and 6 locations
Greg Lawless, IT Manager
Over 400 workstations and 6 locations
Industry experts agree...
Gartner predicts that, through 2020, 99% of vulnerabilities exploited will continue to be the ones known by security and IT professionals...While some of the most crucial phases of the patching process can benefit from human oversight, automation can streamline and execute all of the steps in between, taking a process from days to minutes...
Businesses that embrace automation for patching are sure to improve their security posture and their compliance with regulations, not to mention recognizing significant gains in operational efficiency and resource allocation.
Vijay Kurkal, COO
Resolve Systems
[source]
SET UP A DEMO
The results speak for themselves.

This is a graph of real customer data. This customer already had a patch management system in place, but it wasn't getting the job done. The Lithik Security Manager cleaned up the entire network in a matter of days and kept it there straight on through Patch Tuesday, bringing their risk factor nearly down to zero. That's why we do what we do.











